Information Security Forum (ISF), a nonprofit association that researches and analyzes security and risk management issues has noted that many CISOs are reporting the wrong key performance indicators (KPIs) and key risk indicators (KRIs).
In part-I of the series, we discussed KPIs and KRIs basics to help new leaders understand the importance of KPIs and KRIs. The measured value of KRI should be able to reflect the negative impact it would have on the organization’s KPI. The KRIs are like an early warning system that alerts the management when risk exposure exceeds tolerable limits.
While KPIs as performance indicators help identify the performing and underperforming aspects of the enterprise and provide further guidance on the allocation of resources to the areas that merit more attention. KPI could be better explained by the event which has happened, e.g. the number of breaches, system failures, etc. and the KRI will indicate the risk in future or likely chance of an event happening so that management can act proactively.
The next step is how to write effective KRIs. The COSO paper “Developing Key Risk Indicators to Strengthen Enterprise Management” is very useful guidance on the subject. The risk management experience and consideration of the following points will help in developing effective KRIs.
- The understanding of the organization’s objectives is very important to identify the events that could impact the achievement of those objectives.
- The linkage between top risk and objectives will be an effective indicator of risk.
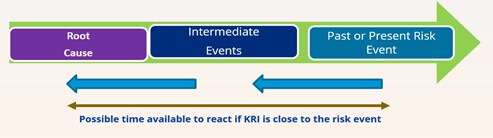
- The best way to identify KRIs is to start with the event that happened in the past or near present. The analysis of intermediate events leading to the main even and root of those intermediate events will help identify the risk.
- The goal is to develop KRIs close to the root cause so that they serve as an early warning as well as able to provide enough time to respond.
- KRIs could be developed close to the intermediate event but they will provide less time to react.
- The development of the KRI process starts with people in the organization especially subject matter experts who have a better understanding of intermediate events or failure points and root cause. Their input will be very important to ensure the key risks are considered.
- As an early-warning indicator, the KRI should be quantitative. The attempt should be made to quantify qualitative information and not ignored.
- Relevant data must be easily accessible, and data mining and analysis should not involve excessive additional costs and resources.
- Measuring KRI involves the analysis of data. The team must agree upon data points considered in measuring KRIs. The data collection, aggregation and correlation method and data points must be agreed upon in advance.
- The consistent and acceptable method for measuring KRIs must be agreed upon in advance.
- An important element of any KRI is the data quality used in measuring KRIs. The data points, external sources and internal sources must be agreed upon to provide the quality data for measuring KRIs.
- External sources are useful in developing KRIs for the risks never faced before.
- There is no internal data that could assist in developing KRIs for emerging risk. The data for developing emerging KRIs could be sourced from external and independent third parties.
- Also, considering certain external data in developing KRIs will be useful from the objectivity perspective and it also helps in addressing biased opinion.
- Aggregating certain KRIs will help in a better understanding of the risk being monitored compared to individual KRIs.
- It’s important not to confuse KRIs and KPIs. The risk indicators are different from performance indicators.
RELATED POST : Key Risk Indicator & Key Performance Indicators Part I


2 Comments