In the last posting – Securing Cloud Data Part I – we discussed the security triad in the context of data security which includes data-at-rest encryption to protect confidentiality, data in transit encryption to protect the integrity, high availability clusters, and failover for availability. The encryption consideration includes data classification, encryption policy, regulatory and compliance requirements, high availability, application integration, support, and key life cycle management.
The Cloud Security Training Series Part II onwards is focused on providing basic conceptual information about cloud security in the context of AWS and Azure. This will help security reviewers, auditors, and risk management personnel.
Cloud computing is the delivery of computing services – servers, storage, databases, networking, software, analytics, intelligence, and moreover the Internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale. The cloud model promotes availability and is composed of five essential characteristics, three service models, and four deployment models.
The risk associated with cloud computing is no different from those applicable to the IT environment within an organization. The difference may originate from the cloud service model, technologies, operations model, and users. In short, people, processes, and technology used in cloud deployment decide the security requirements. The characteristics of cloud computing lead to enormous opportunities as well as risks. The key concerns are related to loss of control, security, integrity, privacy, and availability
Cloud security Training mainly consists of the following domains:
• Architectural Concepts & Design Requirements
• Cloud Data Security
• Cloud Platform & Infrastructure Security
• Cloud Application Security
• Operations
• Legal & Compliance
It will be a very long article to describe in detail the various aspects of AWS and Azure security but knowing certain security areas within AWS and Azure will help.
AWS offers storage choices for backup, archiving, and disaster recovery use cases and provides block, file, and object storage. Amazon Simple Storage Service (Amazon S3) provides developers the ability to write, store, and retrieve data from anywhere on the web through a simple web service interface. The figure below shows the various AWS and Azure data storage choices.
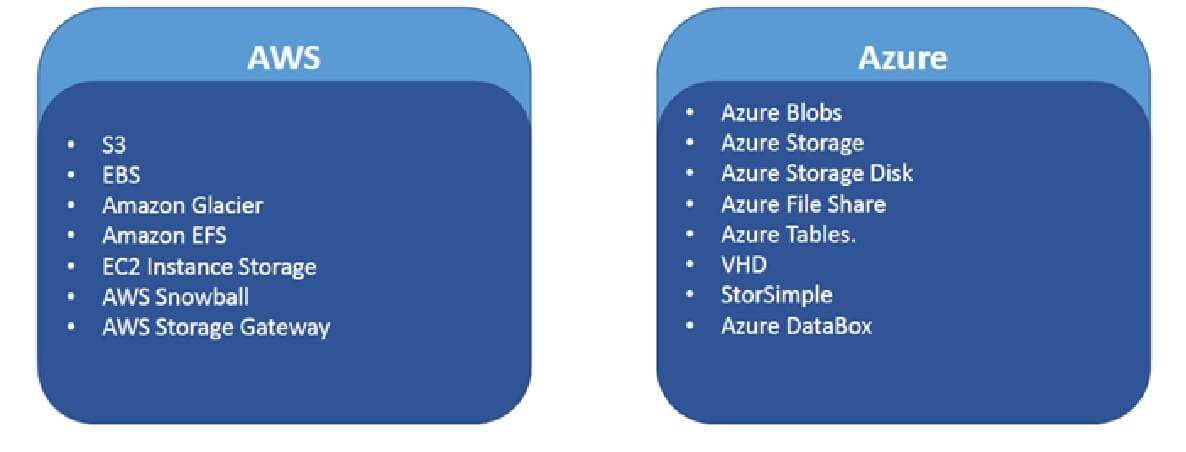
Amazon S3 provides for control of access to Amazon S3 resources and it supports encryption. You can protect Amazon S3 data at rest by using server-side encryption, in which you request Amazon S3 to encrypt your object before it’s written to disks in data centers and decrypt it when you download the object by using client-side encryption. You can protect the data in transit by using Secure Sockets Layer (SSL) or client-side encryption. The AWS Cloud security storage services include Amazon S3, Amazon Glacier, Amazon Elastic File System (Amazon EFS), Amazon Elastic Block Store (Amazon EBS), Amazon EC2, AWS Storage Gateway, AWS Snowball, and Amazon CloudFront
Azure Storage includes Azure Blobs (objects), Azure Data Lake Storage Gen2, Azure Files, Azure Queues, and Azure Tables. Azure Blob storage is Microsoft’s object storage solution for the cloud. Blob storage is optimized for storing unstructured data. All data (including metadata) written to Azure Storage is automatically encrypted using Storage Service Encryption (SSE). Azure Active Directory (Azure AD) and Role-Based Access Control (RBAC) are supported for Azure Storage. Data can be secured in transit between an application and Azure by using Client-Side Encryption, HTTPS, or SMB 3.0. OS and data disks used by Azure virtual machines can be encrypted using Azure Disk Encryption.
RELATED POST:
Securing Cloud Data – Cloud Encryption Considerations Part III

